Avira Phantom Vpn For Ios
The improvement was additionally aimed toward making it simpler for Tor customers to entry the most secure model of Facebook from inside a platform like Tor Browser without having to remember a special onion URL. And the Tor Project’s Bagueros says that Brave has so far shown strong commitment to evolving its Tor implementation to be more and more secure. «If there are 20,000 browsers doing the same factor we don’t thoughts. We think that’s great.» The overwhelming majority of Tor customers are odd people who need management of their privacy online or folks whose web use is censored. Other Tor users are journalists, human rights defenders, home violence survivors, policymakers, diplomats, and academic and research institutions.
If all users close their browsers the darknet ceases to exist and the one hint of its existence are a number of encrypted fragments in the internet browser’s historical past. Traffic analysis of the surface net is a significant reason why companies are using Tor. Traffic analysis permits organisations or hackers to learn the behaviour and interests of subjects or teams, by following the source and vacation spot of web traffic.
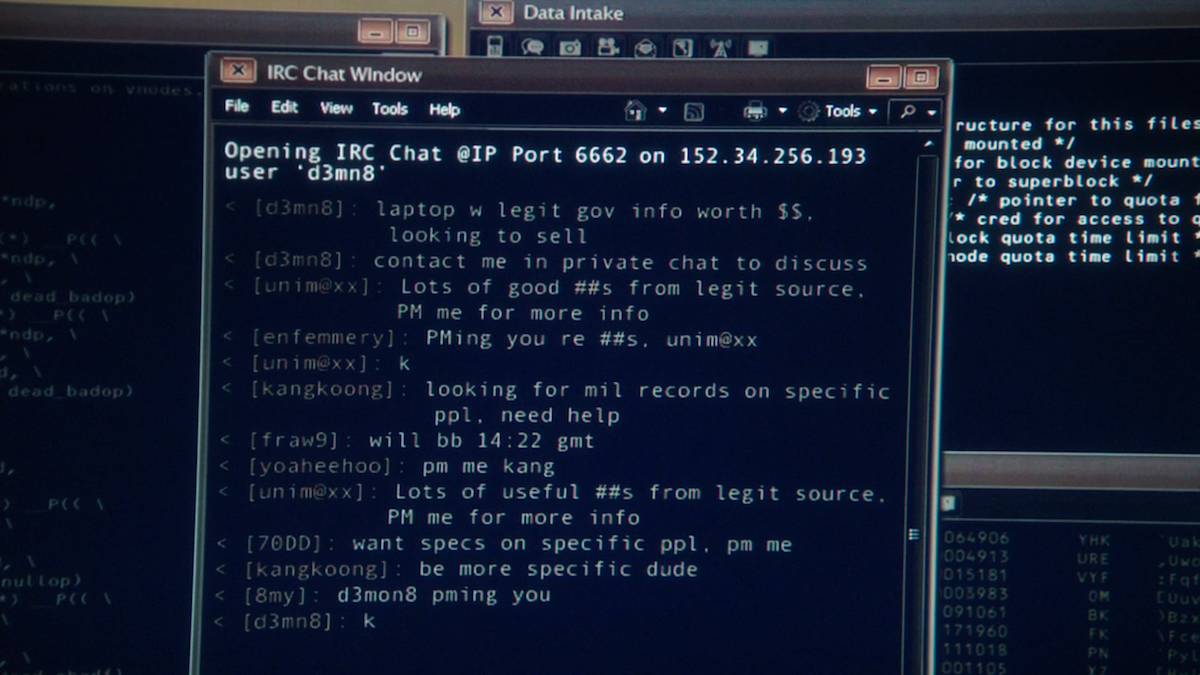
Several illegal activities take place on this darkest part, including baby pornography, monetary fraudulence, drug deployment, and plenty of others. Thus, countermeasures to put a curb on these actions are very much required. The chapter focuses on essentially the most related research areas and potential analysis scopes in the area of the darkish web.
Poking around on the darkish web is where some folks get themselves into trouble. Unlike the deep internet, which accommodates necessary and helpful info, the dark internet is riddled with unlawful and unconscionable activity. One called the Uncensored Hidden Wiki provides some steering to content on the dark net, however it may include illegal web sites. Law enforcement officials operate on the darkish internet to catch people engaged in legal activity.
- It is difficult to trace users in the darknet and so it became a haven at no cost speech and expression, especially in countries where the web is closely policed and blocked.
- For example, educational databases are solely available to college and students, and corporate networks are only available to employees.
- Peer-to-peer networks and self-hosted websites are additionally a part of the darknet.
- Sites here are not indexed by search engines like google as a result of they are merely not accessible to them.
Using Tor Browser With A Vpn
Therefore, most Dark Web customers access these websites using the Tor browser. There are different encryption tools and corresponding browsers such http hydraruzxpnew4af onion as I2P and you need to know the exact URL to be able to entry the location.
The connection would be encrypted between the Tor browser and the Tor exit, hence what the company VPN sees is just encrypted tor site visitors. I solely need browser level protection, which is why I use TOR, in any other case I want all visitors to undergo my community normally. Adding every application to ProtonVPN’s bypass filter is tedious to say the least.
Enter the Tor network, brief for “The Onion Router,” given the many layers of encryption that guard passing data. Tor lives on the perimeter of the web and serves as the underlying know-how of the dark internet—a collection of hidden sites inaccessible by way of an everyday browser and not listed by search engines like google and yahoo similar to Google. The Tor browser—a free obtain—is all you should unlock this hidden nook of the web the place privacy is paramount.
